In this article, I’ll show you how to use custom compliance policies for Intune.
Compliance policies are an important part of securing access to data in Microsoft 365. After all, if possible, only devices that meet our requirements for security should be able to access or edit data locally.
The realization is done by conditional access rules and the compatibility of the device. Compliance policies can be used to define the compatibility of the device. By default, there are already some compliance policies that can be used. These define, for example, whether the device is encrypted or whether a current patch level is installed.
However, I can also use custom compliance policies for Intune to cover more complex requirements. The whole thing works via PowerShell and only for Windows 10/11 devices. Using PowerShell gives us countless possibilities to write our own compliance policies for Intune.
In this example, the following properties are to be checked:
- Manufacturer of the device, in this case we only allow devices from Microsoft.
- Available/installed RAM, in this case at least 16 GB.
- Installed programs, in this case VirtualBox must not be installed. Of course, installing programs for users could be prevented in general, but often the users are equipped with administrator rights on their own clients after all.
With the PowerShell script, there is not really anything to consider except that a string must be returned in JSON format (line 29):
#Get basic information about our machine
$biosinfo = Get-CimInstance -ClassName Win32_ComputerSystem
$manufacturer = $biosinfo.Manufacturer
$RAM = $biosinfo.TotalPhysicalMemory
#Check if it's a Microsoft Device
if ($manufacturer -like "*Microsoft Corporation*") {
$manufacturer = "Microsoft Corporation"
}
else {
$manufacturer = "Unknown"
}
#Calculate RAM
$RAM = ($RAM / 1024 / 1024)
$RAM = [math]::Round($RAM, 0)
#Look for VirtualBox
$installedSoftware = Get-ItemProperty HKLM:\Software\Microsoft\Windows\CurrentVersion\Uninstall\*
if ($installedSoftware -like "*VirtualBox*") {
$virtualBox = "Installed"
}
else {
$virtualBox = "Not Detected"
}
$hash = @{ Manufacturer = $manufacturer; RAM = $RAM; VirtualBox = $virtualBox}
return $hash | ConvertTo-Json -Compress
For custom compliance policies in Intune, we need not only the PowerShell script that collects the information, but also a JSON file that does the evaluation:
{
"Rules":[
{
"SettingName":"Manufacturer",
"Operator":"IsEquals",
"DataType":"String",
"Operand":"Microsoft Corporation",
"MoreInfoUrl":"https://frankeisel.de",
"RemediationStrings":[
{
"Language":"de_DE",
"Title":"Diese Maschine ist nicht von Microsoft!",
"Description": "Wir erlauben nur die Verwendung von Maschinen von Microsoft, bitte kontaktieren Sie uns um weitere Informationen zu erhalten."
},
{
"Language":"en_US",
"Title":"Diese Maschine ist nicht von Microsoft!",
"Description": "Wir erlauben nur die Verwendung von Maschinen von Microsoft, bitte kontaktieren Sie uns um weitere Informationen zu erhalten."
}
]
},
{
"SettingName":"RAM",
"Operator":"GreaterEquals",
"DataType":"int64",
"Operand":16,
"MoreInfoUrl":"https://frankeisel.de",
"RemediationStrings":[
{
"Language": "de_DE",
"Title": "Nicht ausreichend Arbeitsspeicher vorhanden!",
"Description": "Ihre Maschine muss getauscht werden, oder der Arbeitsspeicher muss auf mindestens 16GB erweitert werden. Bitte kontaktieren Sie uns um weitere Informationen zu erhalten."
},
{
"Language": "en_US",
"Title": "Nicht ausreichend Arbeitsspeicher vorhanden!",
"Description": "Ihre Maschine muss getauscht werden, oder der Arbeitsspeicher muss auf mindestens 16GB erweitert werden. Bitte kontaktieren Sie uns um weitere Informationen zu erhalten."
}
]
},
{
"SettingName":"VirtualBox",
"Operator":"IsEquals",
"DataType":"String",
"Operand":"Not Detected",
"MoreInfoUrl":"https://frankeisel.de",
"RemediationStrings":[
{
"Language": "de_DE",
"Title": "Virtual Box Anwendung wurde auf Ihrem System erkannt!",
"Description": "Die Verwendung von VirtualBox ist nicht gestattet. Bitte deinstallieren Sie die Anwendung und versuchen es erneut."
},
{
"Language": "en_US",
"Title": "Virtual Box Anwendung wurde auf Ihrem System erkannt!",
"Description": "Die Verwendung von VirtualBox ist nicht gestattet. Bitte deinstallieren Sie die Anwendung und versuchen es erneut."
}
]
}
]
}
Actually, the JSON file should be quite understandable. Of course, it is important that the SettingsName in the file matches the one in the JSON of our PowerShell script. More information about the JSON file and the available operators can be found at Microsoft. And for the RemediationStrings it is mandatory to have the en_US language, otherwise the validation will throw an error later. In this example, I just copied the same texts again for the en_US language.
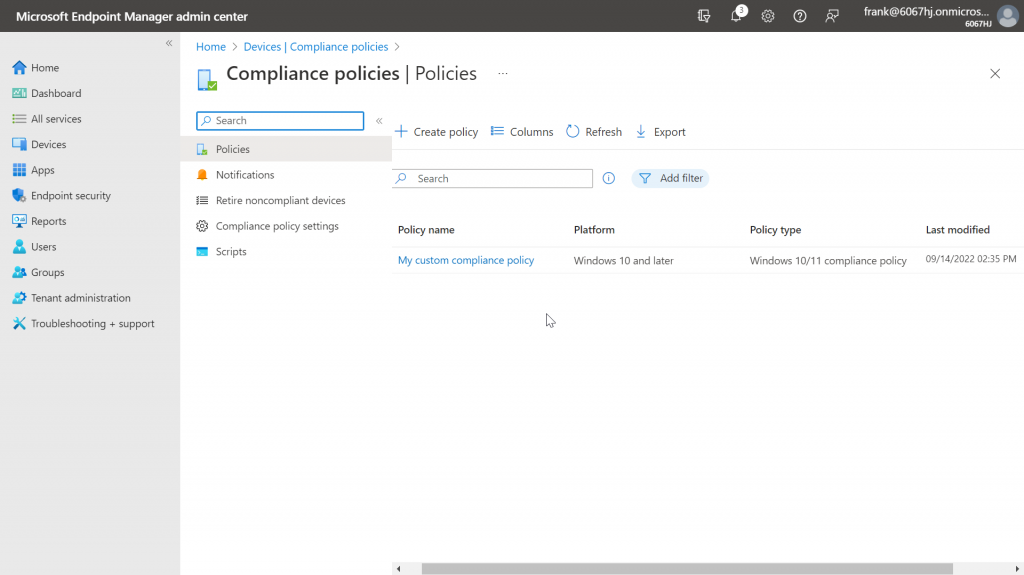
Now we have everything together to create our own compliance policy using our PowerShell script. So we open the Microsoft Endpoint Manager Admin Center and navigate to the compliance policies:
After that, we deploy the PowerShell script we created. This is done in the Scripts section.
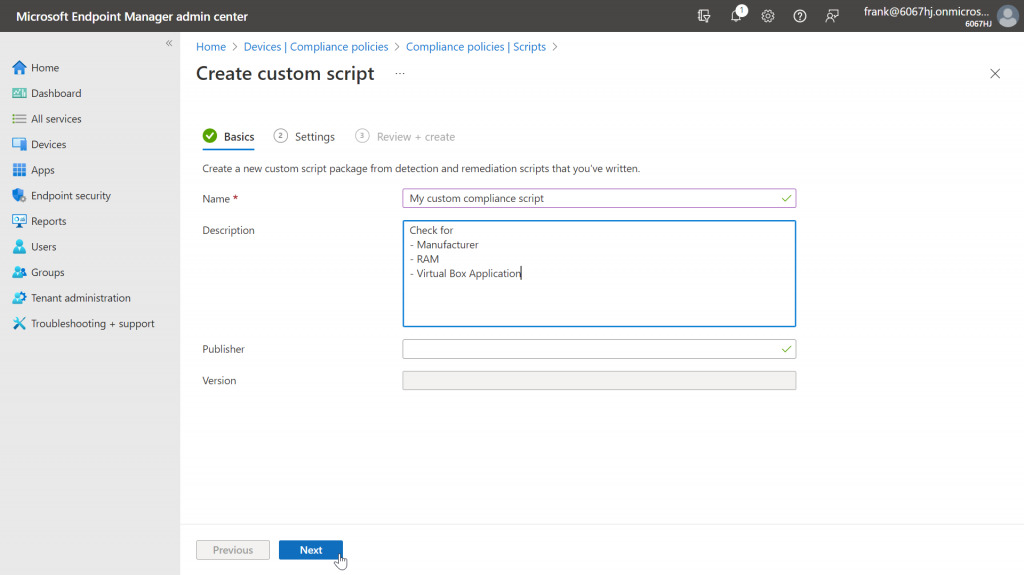
We provide the script a name and, if necessary, a short description of what it does.
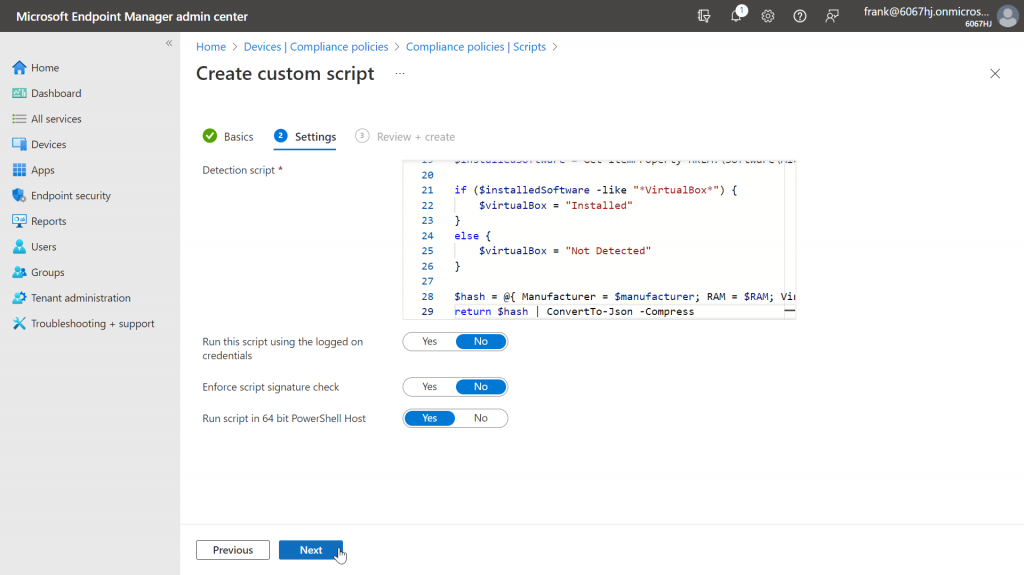
In the next section we add the actual script and can make a few more settings. In our example, however, we take the default settings, which should fit for a large part of the use cases.
After that, we get another short overview of the configurations made and can create the script.
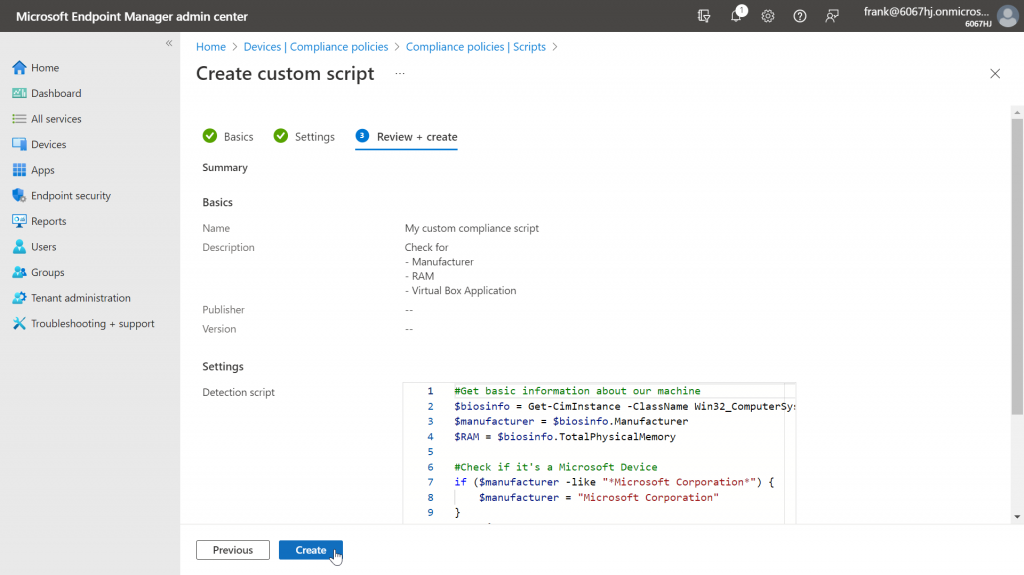
If the creation worked, we can now find our script in the overview.
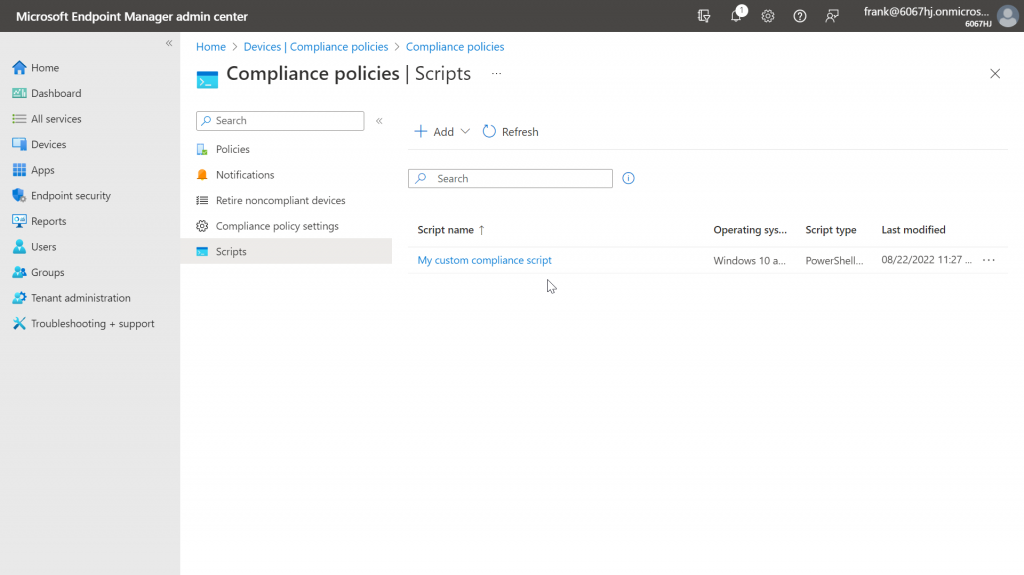
And now we can create a compliance policy that uses our detection script.
We again give the policy an appropriate name and an optional description of what exactly the policy does.
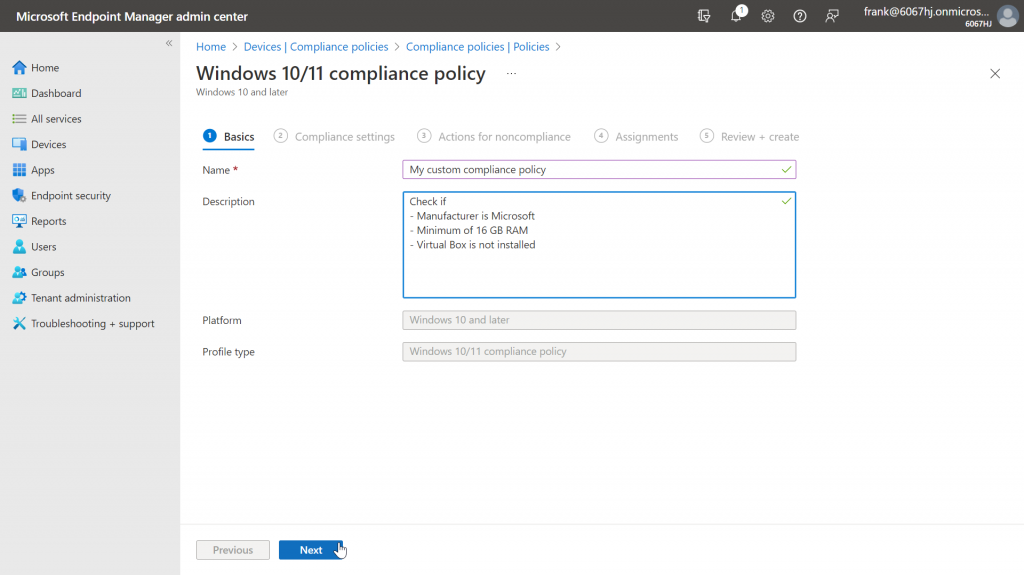
In the next step, we then select the Custom Compliance item and select the script we just uploaded.
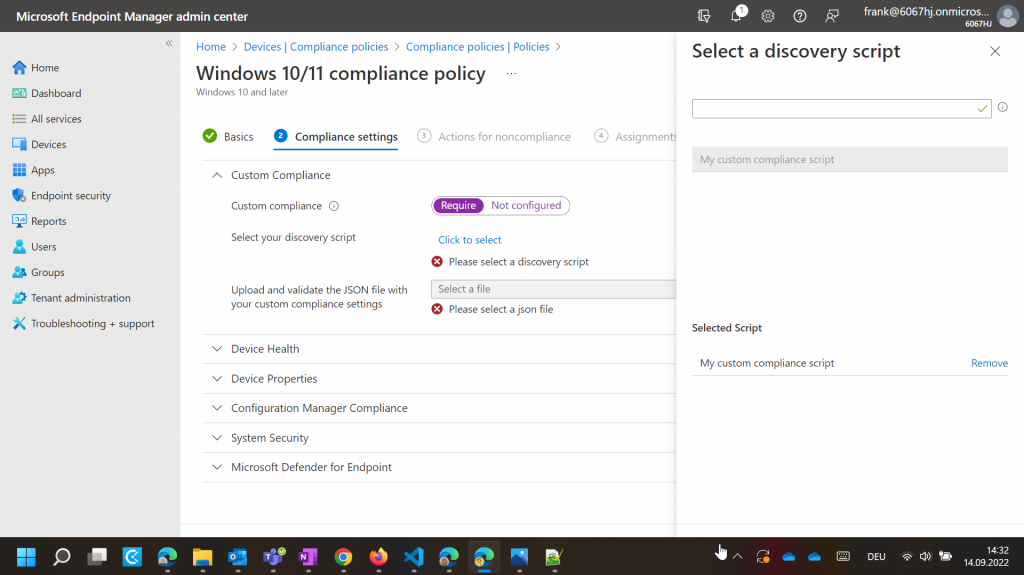
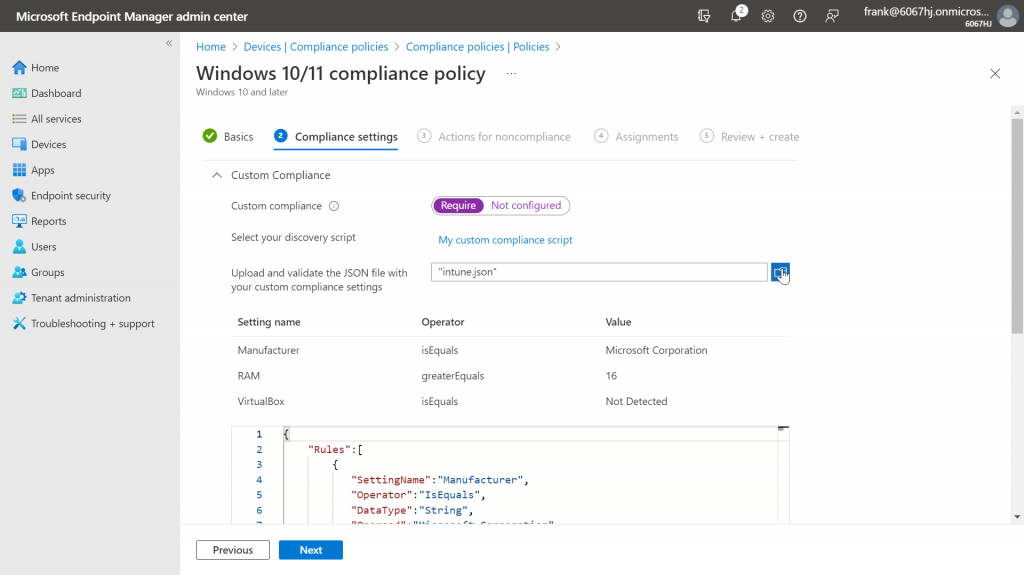
Now we still need to upload the prepared JSON file and have it validated. If no errors occurred during validation, our settings will be displayed accordingly.
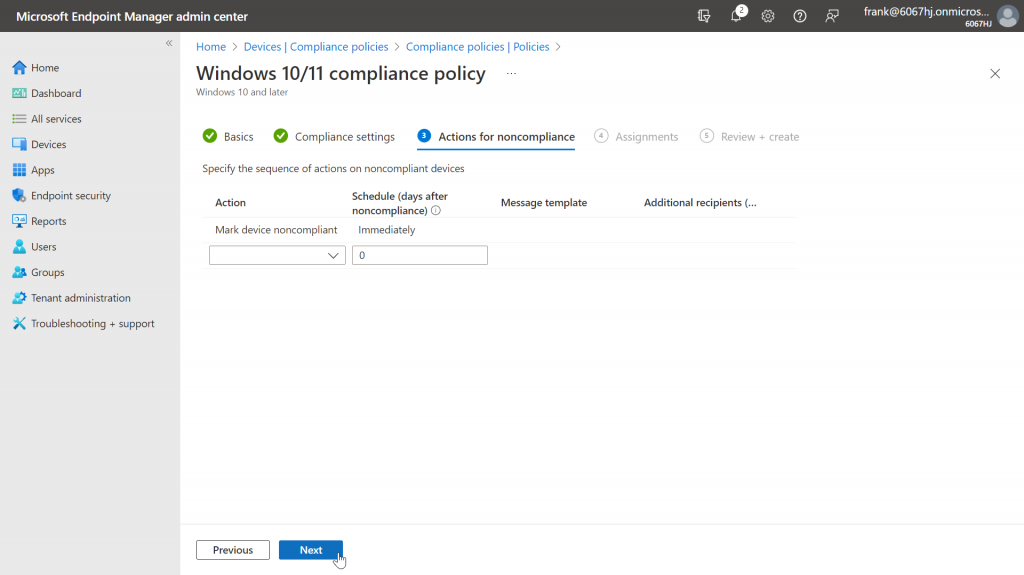
After that, we can make the familiar settings about what should happen when the device is no longer compliant.
The last step is to specify to whom the policy should be applied. In this case, just select All users for simplicity.
Now a short summary of the configurations made appears again, and we can create the policy. After that, the compliance policy appears in the overview.
Now, if we look at the compatibility of our device via the company portal app, we will notice the following:
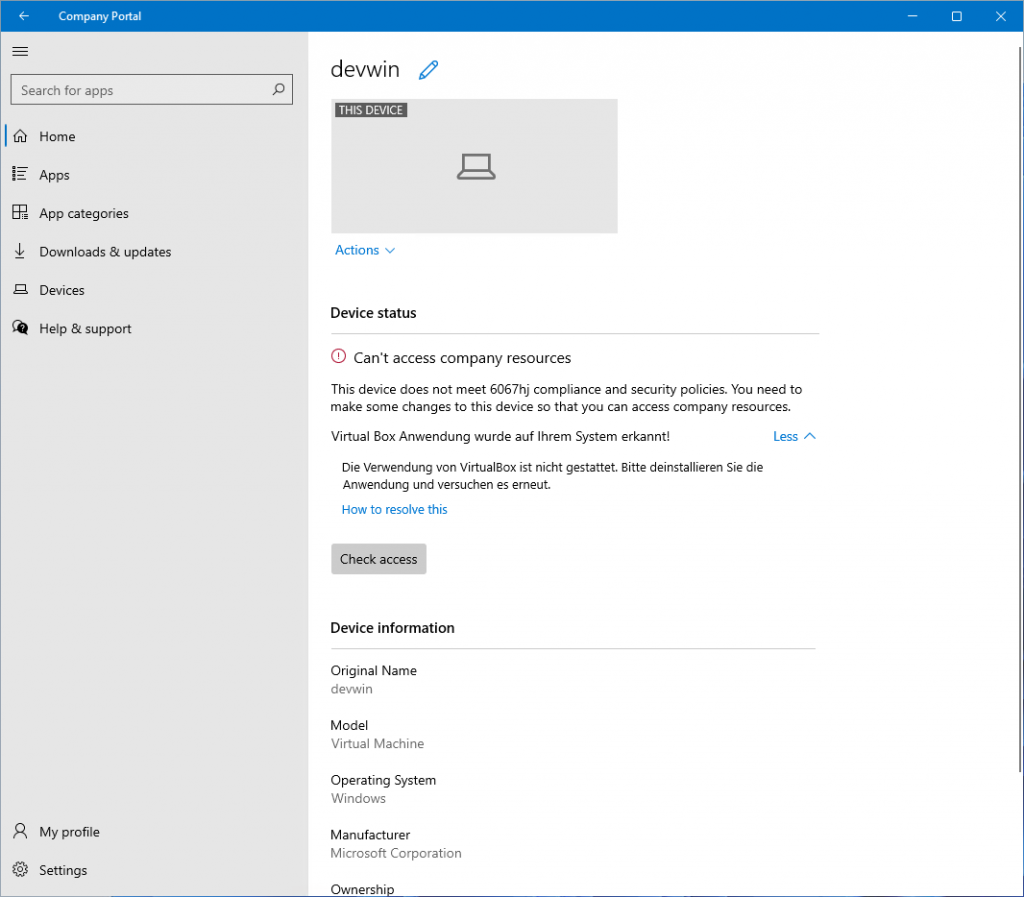
Our PowerShell script has detected that we have installed VirtualBox on the machine without permission and now denies access to the company data in the cloud. The defined texts from the JSON file are also displayed and also offer a possible fix in this case. However, the machine fulfills the other queried parameters (manufacturer and RAM)
Of course, you can also see this in the Microsoft Endpoint Manager Admin Center. There you can see the defined settings and whether they are fulfilled.
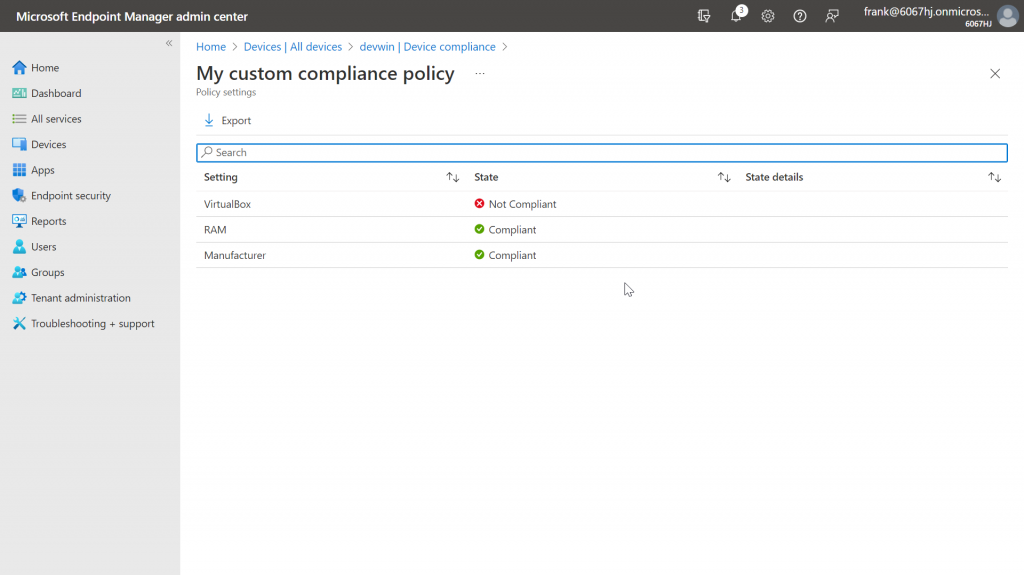
With the ability to write PowerShell scripts ourselves, we now have a powerful tool at our fingertips to determine our compliance of devices ourselves.

[…] This post is also available in English […]